Hiya, so been on the lookout for different services that I could help host for others to benefit from. I think TOR is a great project, and I’d like to contribute. So been thinking about hosting a TOR relay lately, and wondering how people’s experience is with running one? Please correct me if I’m wrong - but as far as I know, it only becomes “scary” to host, if you were to host an exit node? And the only real requirement to host a relay is to have a good internet speed? Mainly wondering people’s experiences with running a relay.
Edit: Very well-timed and relevant upload from Techlore, on how to use Tor just dropped: https://youtu.be/K3wmLvny5tg
All you need is a web browser running Snowflake to help people connect to Tor!
Didnt take long before someone connected, feels good to help!

This is what I did on a Raspberry since snowflake can run as a normal service without a browser, too. The Raspberry then runs 24/7 and I don’t have to care if my browser is running.
Good to know! Thanks
Wow this is neat! Wasn’t aware of this. Is this the same as running a full dedicated relay?
Have already installed and activated it, and will do so on more of my devices.
Snowflake acts as an entry point. A lot of official TOR entry nodes are blacklisted in some contries. Since Snowflake can run basically behind any IP anywhere where a browser is, it is hard to block them. In that way users in suppressed countries can still access the TOR network through Snowflake but the official entry nodes.
Ah I see, good to know. I don’t think my country blocks them, but I’ll try to do some research. It seems like TOR has a nice overview over good and bad ISPs too, if one were to go the route of hosting through a company: https://community.torproject.org/relay/community-resources/good-bad-isps/
Neat.
Too great a chance someone downloads csam through it and I get blamed.
But as far as I understand, thats only a worry for people running exit nodes? Or?
You’re correct, but I still am not comfortable taking the chance.
Just don’t run an exit node? We need more guard and relay nodes anyway. I fail to see the issue.
totally fair
Correct. This is one article that goes over a multi-hop VPN that’s sort of relevant regarding how you, as somebody in the middle of this process, would not see what is being relayed even if you’re closer to the end-user.
(Obviously this isn’t quite as far as Tor goes, but at least it explores the principle.)
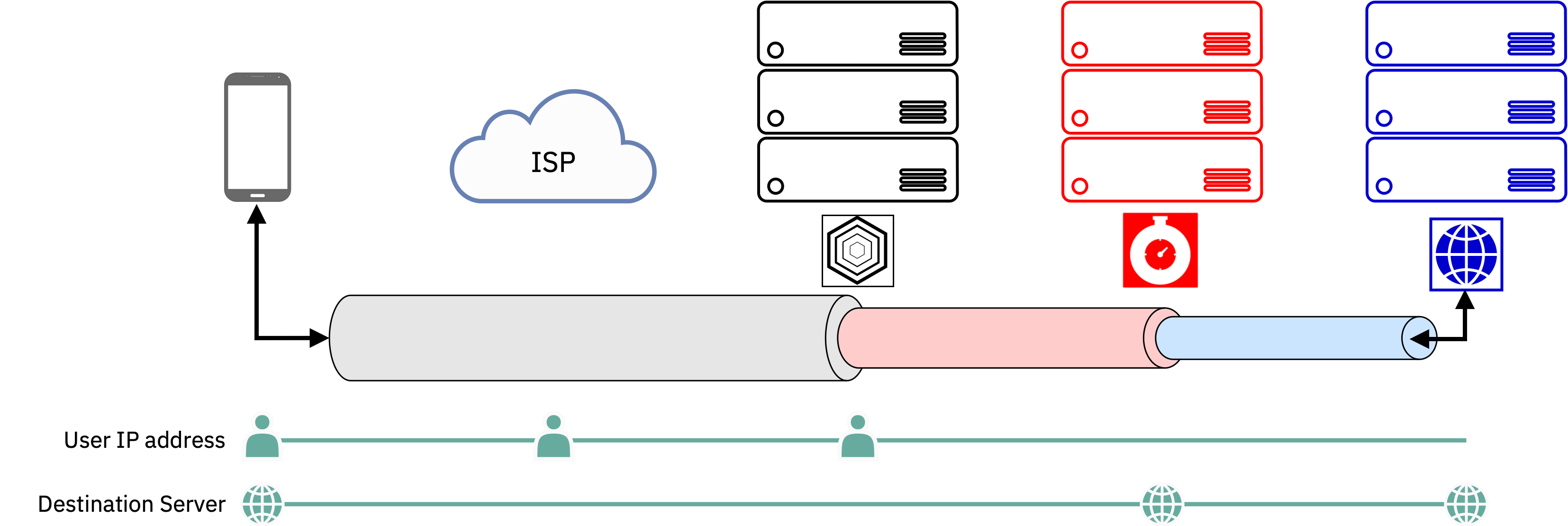
Nice illustration, thanks!
Also: I often see your name in Lemmy posts/comments, and just wanted to say thanks for contributing so much. You come with very valuable and factual information, as far I’ve seen - and I appreciate that :)
Have a nice day 🌻
Running a middle relay for years with no issues.
I did a long time ago and don’t remember much about it other than it just worked. But then I tried again recently and couldn’t get it to work properly. Although that’s probably because I hadn’t played with it in years and was missing something with my configuration.
If you do, do it in a vps. Because, if you do it at home, your isp won’t be too keen on your traffic.
Mainly true for exit relays. I do not recommend trying to run an exit relay from home at all. If you run a middle relay though you should be mostly fine.
Yeah that might be a good idea
I am not.




