As in title. What’s your experience with it? If something isn’t executable, then it has to exploit vulnerability in order to run anything malicious. But does it happen often with mp4, mkv and other files like mp3 or epub?
I assume that if I use updated linux, then I’m mostly safe?
But does it happen often with mp4, mkv and other files like mp3 or epub?
Typically is not possible. Those media files are basically just data files (e.g. like a .txt text file) so media players normally do not look for anything to execute inside them. And frankly people should avoid any media player attempting to execute random code found in media files.
Case in point, the old Windows Media Player + old .wmv files used to be able to direct people to random websites to download/execute malware. Leave it to Microsoft to somehow turn a movie file into malware https://security.stackexchange.com/questions/106188/can-a-rogue-wmv-file-hijack-windows-media-player
It’s not about a media player ‘attempting to execute random code’ - an exploit is found which lets it run a command that it shouldn’t. You used to be able to jailbreak phones by loading a .pdf file that used an exploit to gain root privileges and execute code. It wasn’t a feature of the PDF reader. It was a bug that could be exploited when a specific string of characters was entered to effectively crash the pdf reader and let it run its own code instead.
A txt could easily contain malware - any file could.
PDF is a complicated format, and the hacking vectors are often thanks to embedded javascript, or vulnerabilities in the parsing libraries.
‘avi’ is technically a container format, kind of like ‘zip’, it can contain more than video/audio.
That said, I’ve been pirating movies since the mid 1990’s and haven’t gotten hacked through a .avi/.mkv/etc. The ‘bad stuff’ was always in a obvious .exe/.bat or some sort of executable, but sometimes named to exploit people, eg ‘foomovie.avi.exe’.
If in doubt, run your videos using mplayer on Linux and not on Windows, most of that stuff tends to target the easier to exploit and more commonly deployed systems, eg Windows.
Yesh - the huge majority of malware in relation to piracy is from people deliberately running ‘setup.exe’ from some untrusted source, ignoring or overriding AV warnings and then wondering what went wrong. Its not from movie files and it certainly not from movie files on Linux.
True. This is something to worry when securing the network of a large corporation & governments. Not for the average pirate
More likely is a specific file-naming trick that lets you use right-to-left writing to make a file look like something it’s not. When it’s written backwards, you can make iva.scr look like rcs.avi, and the target will just think it’s a video file when it’s actually an executable. If you’re not paying attention, you may not notice that Windows Explorer shows a .avi extension but lists the file as an executable. Hell, if you open the file directly from your torrent app, it may not even list the file type at all. In effect, it’s not hiding a payload in a video file, just disguising the payload as a video file.
I assume that if I use updated linux, then I’m mostly safe?
I don’t know why Linux users think they’re completely immune to malware. Yes it’s very unlikely that something gains root access if you run it without super-user privileges, but that program can still access your home folder and look at all your private data.
Probably because the vast majority of the pirate software available is for Windows, and there’s no way that program will run natively on Linux.
I mean, if I download a movie from freevirus(dot)com it is most likely that the movie will be a .mp4.exe and not a .mp4.sh.
And even if it is a .sh file, you’d still have to change it’s permissions before it could do anything
If wine installed, there is a big chance that the exe can be started by simply doubleckicking on it. A lot of windows programs can run in wine without any specific setup, e.g. a basic crypto miner.
That’s why I said natively.
I agree with what you said, but it’s also important to clarify that a lot, but a lot of pirate Windows software doesn’t run on Linux with just two clicks, even with Wine, it doesn’t look like it but check c/LinuxCrackTips.
Games like Forza Horizon 5 or Monster Hunter World (just to mention two examples I have in mind) need to run under a specific Wine prefix that is usually not as simple as searching on internet which prefix to use, it’s pure proof and pain of trying until the game miraculously opens, and many times if it’s not the problem of the prefix itself it’s because you have to add specific environment variables, sometimes you need specific dependencies that you don’t have any idea, sometimes said dependency is DX11
I think that even sometimes is worse, Days Gone for example ran with lag because I used “system sync” and not “esync” and here it wasn’t even the prefix problem, it was of that, nobody told me, I had to try it myself.
And not to mention that when you want to download pirated games on Linux it’s best that they’re a crack made by Empress, since she/he has to work specifically with Proton binaries to make it work on the Steam Deck, look Resident Evil 4 Remake where Empress had to create a crackfix specifically for Linux (better Linux support than Capcom herself, heh) because the game to Linux users under Wine/Proton threw an error, but the same game on Windows didn’t suffer from that.
And finally, there are programs that just don’t run because “Your GPU isn’t supported”, that mean that the program it’s not detecting the driver, so I find it hard for something like a cryptominer to work in Linux under Wine, but of course it can happen.
Personally I use Bottles, since Bottles allows me to manage my prefixes and their processes in an orderly and clean way with graphical interface and within a flatpak container (which I know, it is not necessarily the safest thing, but it is inside the Wine container, and the Flatpak container that gives me more security) but within Bottles I can close all the programs and processes that a prefix has open with a click, if I had Wine installed at system level where the programs ran to two clicks I actually would worry too much because I would not have the same level of management as in Bottles.
Its mostly harmless. Here is a paper from 2019
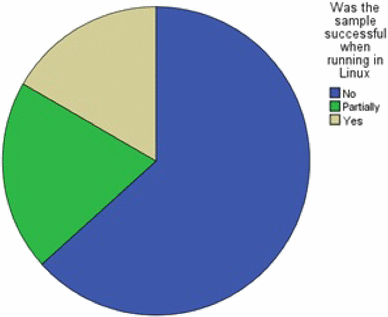
Curious if those percentages are still true, Windows compatability has improved a lot in the past 4 years.
It is very unlikely that someone is gonna bother creating malware for Linux unless it’s a targeted attack
Eh. I only ever open pirated movie/video files from within a docker container (Plex server) running in a VM. I don’t think I have much to worry about.
We don’t - but the risk is minuscule compared to windows. The actual chance of finding some working Linux malware in the wild is practically zero.
Oh no, it would be a shame if someone saw my naughty pictures.
To my knowledge, Ive never downloaded any malware from a pirated movies/music/books. The possibility is always there when downloading from unverified sources. That said if you stuck to the sites listed in the wiki you should be fine.
Very unlikely but not impossible. Always check the comments when downloading torrents to make sure they are legit.
Someone with that kind of exploit would likely try to target something valuable like big companies, rich people, governments and not you.
It’s always useful to add another machine to your botnet.
And get it fixed quickly? Or skip on a huge potential payout from some company?
For the price of that kind of exploit on the black market? Nah.
it’s almost impossible that some state sponsored attacker will waste a 0day to attack random people downloading the latest movie from torrent. And when it happens all the news will talk about it
State sponsored hackers are a very small percentage of the threat actors out there. Also - they don’t need to exploit a zero day if you are willingly launching something on your machine.
I would never make assumptions when sailing the high seas! That said - seems kinda unlikely to me. Not impossible. Just unlikely. :)
Movies? Usually it’s like “go to malware.com for the password” but you wont get infected from movie files.
I had dodged stuff before when I downloaded software, I’d be weary of anything you give permission to run on your pc. But for movies and music etc, I check what files I’m getting. While this doesn’t eliminate the risk of malware cased in a .mkv, I only download on a Linux VM, and usually first open on MacOS.
I meant dodgy stuff from downloading software. Damn autocorrect.
As far as anyone knows there is no way to put malicious code in a video file. What you should be worrying about is how you get those files.
If you’re torrenting then you have to worry about copyright trolls contacting your ISP. If you’re using file-hosting websites just vet your downloads and make sure you don’t run any sketchy executable files. And it should go without saying, but don’t escalate privileges for unknown programs.
Not entirely true as you can put malicious code in anything. The bigger question is whether or not your video player is susceptible to that type of attack. I would say the likelihood is low but not impossible. The best defense would be to make sure whatever video player you do use is fully up to date.
So real player is out then?
If you click on The.dictator.torrent.exe you will certainly get a virus
Typically what I see are low effort attacks where an attacker puts out an obfuscated file online (like fast.and.furious.5.mov.exe) in an attempt to trick the user in executing the file. Most of the risk running comes from running pirated software where cracks and activators often come bundled with other malware. Or running outdated Plex server that is exposed to the internet… Take a look how Lastpass got hacked…












